As my posted before, we replaced the firewall on Shanghai office to Fortigate 60B and it used two dynamic PPPoE DSL for internet and VPN connection. Everything works smoothly but we found that the VPN tunnel can't create automatically and needs traffic triggered by dialup side to create the VPN tunnel. The tunnel can't be created by dialup server. It means that if users behind of dialup server and need to access to the resource behind of dialup client but VPN tunnel is not created, the access will fail. It is annoying.
To solve this issue, we need to enable auto-negotiate on Fortigate dialup client side through CLI mode.
Please refer the example configuration as below:
========================================
config vpn ipsec phase2
edit "VPN_IKE"
set auto-negotiate enable
set keepalive enable
set phase1name "VPN"
set proposal aes128-sha1
set dhgrp 1
set dst-subnet 192.168.11.0 255.255.255.0
set src-subnet 192.168.22.0 255.255.255.0
next
end
========================================
After enable the auto-negotiate function on phase2 IKE, the VPN tunnel can create automatically and I don't have to worry about users can't access to remote resource through VPN tunnel.
Thursday, December 24, 2009
Wednesday, December 23, 2009
Fortigate -- Setup LDAP server for SSL-VPN client authentication on Fortigate
Our office located on three area and have to provide SSL-VPN for mobile users to connect to access office resource. We are using Local user accounts on Fortigate for SSL-VPN client authentication.If users requested that he/she needs to access to all office's VPN, i need to create three accounts. It is not smart.
To simplify the process and centralize the authentication, I decided to use Windows 2008 AD as LDAP server and setup LDAP authentication on three fortigate to reduce the management process.
On Windows 2008:
1. Create a group on AD for SSL VPN clients. (SSLVPN Group)
2. Create an account on AD and as a member of "SSLVPN Group"
On Fortigate:
3. User -> Remote, on LDAP tab, click "Create New" icon.
4. Fill in the information. (See below for example)
- Name: SSLVPN Client
- Server Name/IP: 192.168.2.2
- Server Port: 389 (default)
- Common Name Identifier: sAMAccountName (Can select one of AD account attributes.
ex: cn or userPrincipalName)
- Distinguished Name:
This method can work with group restrict to manage account. Please refer Note below.)
- Bind Type: Regular
- Filter: (&(objectcategory=group)(member=*)) <-- this is default value
- User DN: cn=user1,ou=users,ou=tpe,dc=ppp,dc=corp (For AD authentication to get
the AD information)
- Password: password
- Secure Connection: not selected
Note:
Because we need to have a group to restrict the user account on SSL VPN accessing.
We need to add one more setting on Fortigate through CLI.
TPE-FW #config user ldap
TPE-FW (ldap) #edit "SSLVPN"
TPE-FW (SSLVPN) #set group "cn=SSLVPN Group,ou=Permission_Group,ou=TPE,dc=ppp,dc=corp"
end
Refer the document:
http://kb.fortinet.com/kb/microsites/search.do?cmd=displayKC&docType=kc&externalId=13141&sliceId=1&docTypeID=DT_KCARTICLE_1_1&dialogID=1326745&stateId=0%200%201324960
To simplify the process and centralize the authentication, I decided to use Windows 2008 AD as LDAP server and setup LDAP authentication on three fortigate to reduce the management process.
On Windows 2008:
1. Create a group on AD for SSL VPN clients. (SSLVPN Group)
2. Create an account on AD and as a member of "SSLVPN Group"
On Fortigate:
3. User -> Remote, on LDAP tab, click "Create New" icon.
4. Fill in the information. (See below for example)
- Name: SSLVPN Client
- Server Name/IP: 192.168.2.2
- Server Port: 389 (default)
- Common Name Identifier: sAMAccountName (Can select one of AD account attributes.
ex: cn or userPrincipalName)
- Distinguished Name:
ex1: ou=TPE,dc=ppp,dc=corp (User account need to belong to "TPE" ou for authentication.
the account in other ou or container (no matter parent or syb) will not be allowed.
ex2: dc=ppp,dc=corp (user can belong to any ou or container under domain for authenticationThis method can work with group restrict to manage account. Please refer Note below.)
- Bind Type: Regular
- Filter: (&(objectcategory=group)(member=*)) <-- this is default value
- User DN: cn=user1,ou=users,ou=tpe,dc=ppp,dc=corp (For AD authentication to get
the AD information)
- Password: password
- Secure Connection: not selected
Note:
Because we need to have a group to restrict the user account on SSL VPN accessing.
We need to add one more setting on Fortigate through CLI.
TPE-FW #config user ldap
TPE-FW (ldap) #edit "SSLVPN"
TPE-FW (SSLVPN) #set group "cn=SSLVPN Group,ou=Permission_Group,ou=TPE,dc=ppp,dc=corp"
end
Refer the document:
http://kb.fortinet.com/kb/microsites/search.do?cmd=displayKC&docType=kc&externalId=13141&sliceId=1&docTypeID=DT_KCARTICLE_1_1&dialogID=1326745&stateId=0%200%201324960
Fortigate -- 60B two PPPoE (Dynamic IP, Gateway) create IPSec VPN
We have two PPPoE with dynamic IP address in the Shanghai office. In the past days, we used DrayTek Virgo2950 as firewall and created IPSec VPN with other offices(Taipei, Hangzhou and San Jose). The connections works normally.
Recently, we purchased Fortigate 60B and want to replace the Virgo2950 as firewall in the Shanghai office. I have to setup FG 60B to create VPN tunnel through two PPPoE to the other offices.
To Hangzhou and San Jose need go through WAN1
To Taipei and IDC need go through WAN2
I got some issues on the default gateway because that we used dynamic IP with dynamic gateway. I can't setup fixed default route on the FG. For this reason, I did not have sufficient routing information for hosts to communicate with remote hosts. Users can access to internet but can't access to remote resource. After some research and google some documents, i got the solution and make it works as our demand.
This memo will forcuse on how to create VPN tunnel and routing to use two PPPoE to access other office resource. It will not content detail steps on all the configurations.
Shanghai FG:
1. Create address for each office network.
2. Create VPN Phase1 and Phase2.
For the Phase1, there have some items need to note.
※Pre-Share Key must same on both VPN peers.
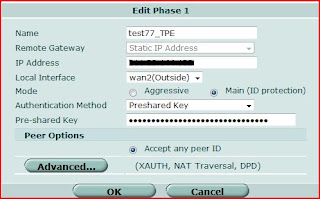
※Because the FG VPN can not dial-up automatically and will disconnect the tunnel if no traffic through the VPN tunnel. To make sure the connection keep alive. "Dead Peer Detection" must be selected.
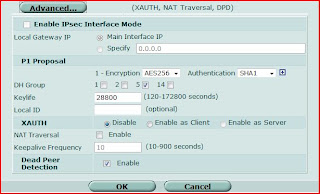
For the phase2
※To make sure the autokey keep alive, "Autokey Keep Alive" must be enabled.
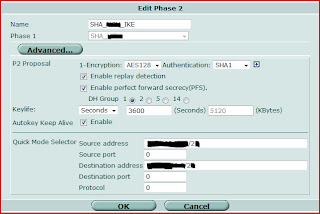
3. Create Firewall Policy
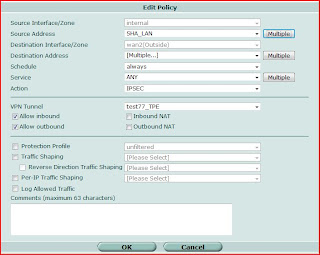
4. Create Route Policy
This is an important section that need to pay attention.
(If you lost this part, you might connect to remote VPN gateway, but you can't access any hosts behind of remote VPN unit.)
Because I don't have fixed gateway to set on the Static Route, I used Policy Route to set the direction of the flow to correct WAN port as i wished.
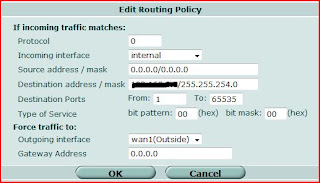
For example, i want to direct the flow to destination address by going through WAN1 Port.
On the edit page, I selected "Internal" as incoming interface and let the source address as defaul.
I filled in the remote subnet as distination address. For outgoing interface, i selected WAN1 as i wished and let the Gateway as blank ( 0.0.0.0).
When all the configuration done, you can start to verify the VPN connection and enjoy your VPN connections through PPPoE.
Recently, we purchased Fortigate 60B and want to replace the Virgo2950 as firewall in the Shanghai office. I have to setup FG 60B to create VPN tunnel through two PPPoE to the other offices.
To Hangzhou and San Jose need go through WAN1
To Taipei and IDC need go through WAN2
I got some issues on the default gateway because that we used dynamic IP with dynamic gateway. I can't setup fixed default route on the FG. For this reason, I did not have sufficient routing information for hosts to communicate with remote hosts. Users can access to internet but can't access to remote resource. After some research and google some documents, i got the solution and make it works as our demand.
This memo will forcuse on how to create VPN tunnel and routing to use two PPPoE to access other office resource. It will not content detail steps on all the configurations.
Shanghai FG:
1. Create address for each office network.
2. Create VPN Phase1 and Phase2.
For the Phase1, there have some items need to note.
※Pre-Share Key must same on both VPN peers.

※Because the FG VPN can not dial-up automatically and will disconnect the tunnel if no traffic through the VPN tunnel. To make sure the connection keep alive. "Dead Peer Detection" must be selected.

For the phase2
※To make sure the autokey keep alive, "Autokey Keep Alive" must be enabled.

3. Create Firewall Policy

4. Create Route Policy
This is an important section that need to pay attention.
(If you lost this part, you might connect to remote VPN gateway, but you can't access any hosts behind of remote VPN unit.)
Because I don't have fixed gateway to set on the Static Route, I used Policy Route to set the direction of the flow to correct WAN port as i wished.

For example, i want to direct the flow to destination address by going through WAN1 Port.
On the edit page, I selected "Internal" as incoming interface and let the source address as defaul.
I filled in the remote subnet as distination address. For outgoing interface, i selected WAN1 as i wished and let the Gateway as blank ( 0.0.0.0).
When all the configuration done, you can start to verify the VPN connection and enjoy your VPN connections through PPPoE.
Subscribe to:
Comments (Atom)
