Recently, we purchased Fortigate 60B and want to replace the Virgo2950 as firewall in the Shanghai office. I have to setup FG 60B to create VPN tunnel through two PPPoE to the other offices.
To Hangzhou and San Jose need go through WAN1
To Taipei and IDC need go through WAN2
I got some issues on the default gateway because that we used dynamic IP with dynamic gateway. I can't setup fixed default route on the FG. For this reason, I did not have sufficient routing information for hosts to communicate with remote hosts. Users can access to internet but can't access to remote resource. After some research and google some documents, i got the solution and make it works as our demand.
This memo will forcuse on how to create VPN tunnel and routing to use two PPPoE to access other office resource. It will not content detail steps on all the configurations.
Shanghai FG:
1. Create address for each office network.
2. Create VPN Phase1 and Phase2.
For the Phase1, there have some items need to note.
※Pre-Share Key must same on both VPN peers.
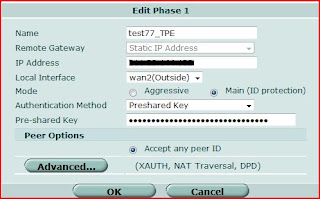
※Because the FG VPN can not dial-up automatically and will disconnect the tunnel if no traffic through the VPN tunnel. To make sure the connection keep alive. "Dead Peer Detection" must be selected.
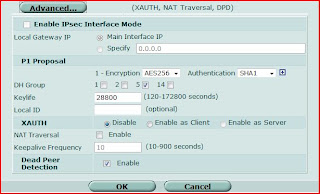
For the phase2
※To make sure the autokey keep alive, "Autokey Keep Alive" must be enabled.
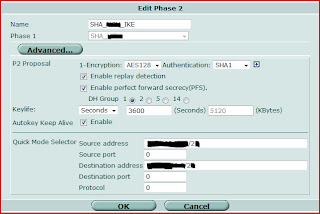
3. Create Firewall Policy
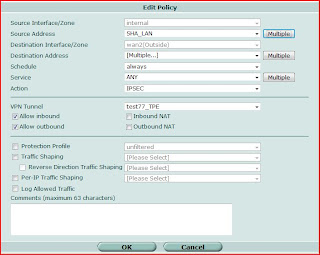
4. Create Route Policy
This is an important section that need to pay attention.
(If you lost this part, you might connect to remote VPN gateway, but you can't access any hosts behind of remote VPN unit.)
Because I don't have fixed gateway to set on the Static Route, I used Policy Route to set the direction of the flow to correct WAN port as i wished.
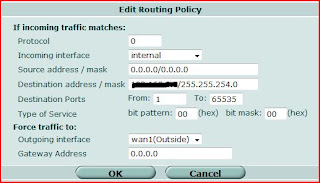
For example, i want to direct the flow to destination address by going through WAN1 Port.
On the edit page, I selected "Internal" as incoming interface and let the source address as defaul.
I filled in the remote subnet as distination address. For outgoing interface, i selected WAN1 as i wished and let the Gateway as blank ( 0.0.0.0).
When all the configuration done, you can start to verify the VPN connection and enjoy your VPN connections through PPPoE.
This is very educational content and written well for a change. It's nice to see that some people still understand how to write a quality post! free vpns
ReplyDeleteI truly value this superb post that you have accommodated us. I guarantee this would be helpful for a large portion of the general population. www.lemigliorivpn.com
ReplyDeleteA blog that mushroomed from visual illumination.
ReplyDelete192.16801
A very awesome blog post. We are really grateful for your blog post. You will find a lot of approaches after visiting your post. https://192-168-i-i.com
ReplyDeleteMulti-line slot machines have become extra in style the rationale 1xbet korea that} 1990s. These machines have multiple payline, that means that visible symbols that are not aligned on the main horizontal could also be} considered as winning combinations. Traditional three-reel slot machines commonly have one, three, or five paylines whereas video slot machines could have 9, 15, 25, or as many as 1024 totally different paylines. Most settle for variable numbers of credits to play, with 1 to 15 credits per line being typical.
ReplyDelete